Data Storage and Cloud Information
1) High level flow of data
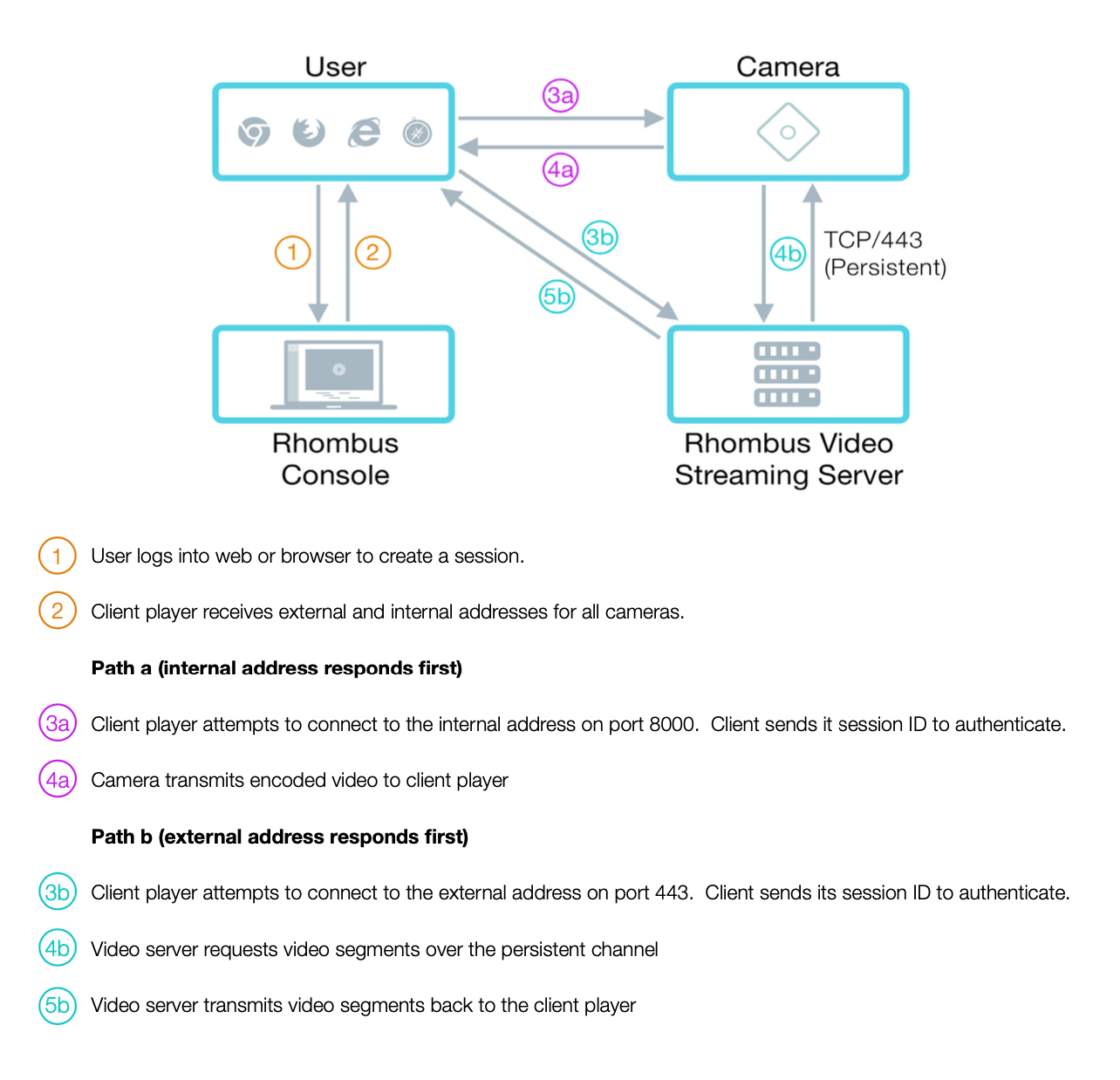
2) Camera Security, Apps, and Web use follows the following protocols
- All video is LUKS AES-256 encrypted
- All communication with the cloud storage is done using TLS 1.2, AES-128 bit encryption
- Mutually authenticated client and server side certificate verification to prevent man in the middle attacks
- Regular 3rd party security audits are performed
- No open inbound ports
- All logins are monitored for anomalous logins
- Hosted on AWS VPC with internal and external access isolated completely
- Complete end to end encryption with all data encrypted both at rest and in-transit
- All passwords are stored using strong one way hashing algorithms
- All media is fully encrypted with redundancy using SSE KMS
- Audit logging from internal and external clients is kept for all access
- Protection against denial of service attacks
- Multi-tenant Security
4) Regulations
National Defense Authorization Act (NDAA)
House Resolution 5515, better known as the John S. McCain National Defense Authorization Act (NDAA), was signed into law in 2018. The NDAA bans U.S. government agencies, contractors, and grant or loan recipients from using products manufactured by certain companies, primarily due to cybersecurity concerns.
The cameras are fully NDAA-compliant and made with high-quality components from whitelisted vendors
The cameras are fully NDAA-compliant and made with high-quality components from whitelisted vendors
SOC 2
Service Organization Control 2 (SOC 2), developed by The American Institute of Certified Public Accountants (AICPA), SOC 2 is a set of information security policies and procedures specifically created for service providers that store customer data in the cloud.
The cameras use SOC 2 Type II certified data centers to protect customer data following the strictest standards.
The cameras use SOC 2 Type II certified data centers to protect customer data following the strictest standards.
CCPA
The California Consumer Privacy Act (CCPA) is a consumer privacy law passed in 2018. Under the CCPA, companies must notify users if they intend to monetize their data and provide the right to opt out of that monetization.
The cameras provide easy-to-use tools to aid compliance with the CCPA, including customer reports and customer data purges.
HIPAA
The Health Insurance Portability and Accountability Act (HIPAA) was created to modernize the flow of healthcare information and specifies requirements to protect the Personal Health Information (PHI; also referred to as PII or Personally Identifiable Information) of patients.
The cameras improve HIPAA compliance by documenting & protecting PHI access.
GDPR
The General Data Protection Regulation (GDPR) is a set of data privacy laws passed in the European Union in 2018. These regulations guide how organizations handle the personal data of the end-users that interact with them.
Our primary camera distributor does have experience with GDPR deployments and data processing agreements so that companies stay in full compliance.
PCI
Payment Card Industry Compliance (PCI) is a set of security standards that any company that accepts or produces credit cards must follow.
Our primary camera distributor helps organizations meet PCI standards by protecting cardholder data and sensitive authentication data.
BIPA
The Biometric Information Privacy Act (BIPA) is a law passed in several U.S. states that pertains to the collection and storage of biometric information such as fingerprints, voiceprints, and scans of the hand or face geometry.
The platform used includes flexible AI settings that allow companies to enable or disable biometric data such as facial recognition as needed to comply with BIPA.
The platform used includes flexible AI settings that allow companies to enable or disable biometric data such as facial recognition as needed to comply with BIPA.
5) Local camera storage and cloud recording
Local Recording
On each camera, H.264 encoded video is stored in 2 second segments on the local /ext4 filesystem. The size of each segment varies substantially based on the amount of content captured. Light, movement, and area under purview are the biggest variables, and can cause segments to fluctuate from as small as 20 KB to as large as 500 KB.
The storage mechanism works like a circular buffer, expunging old data only when new data needs to be written. This creates a fairly constant sliding window of time available to view, typically around 15 or 45 days, depending on storage model. Once data has been expired, it is no longer available for viewing.
Cloud Recording & Policy Events
When Cloud Archiving is enabled on a camera, segments of locally stored footage are continuously being sent directly to our cloud storage service (Amazon S3). Once enabled, all past footage will be streamed from the cloud, regardless of WAN or LAN locality. However, viewing live footage still defaults to LAN if the viewer is on the same local network.
Policy events are configured to intelligently upload content to the cloud where more substantial analysis can take place. Selective video clips are uploaded in 30 second blocks, finding a balance between consuming upload bandwidth and identifying activity. The camera itself does a first pass of analysis, further restricting uploads to only content worth analyzing. The bandwidth usage for policy events varies significantly by the amount of activity the camera detects.
